# OSEP - Evasion Techniques and Breaching Defenses
https://help.offensive-security.com/hc/en-us/articles/360040153912-Can-I-blog-about-any-Offensive-Security-courses-I-have-taken-
I signed up for the class when it was first announced and signed up for the exam the first day it was available. (February 2nd)
I just turned in my exam report for the OSEP Exam and pending approval of my documentation I passed.

I got my original OSCP back in 2012 and I've been using security distros since [@muts made Whoppix 2.7](https://www.youtube.com/watch?v=6M78SRX9ZMA). I truly believe it's critical to stay up to date in this industry. Albeit this is something Offensive Security has NOT been known for doing. It takes a lot to admit when you have made a mistake.
For background sake these last few years I've taken 2 Spectre Ops classes, 2 Dark Side Ops classes, 4 SANS courses and this year I have finished Hack The Box: Dante, Cybernetics, Offshore, and Rasta. I'm excited to see Offensive Security is updating their content and proctoring their exams. This industry has a major problem with sharing writeup's and there is no easy fix.
From taking the class I can say for $1200 you get some serious bang for your buck. Expect to spend 120 hours in the class after reading the 700 page pdf and listening to 20 hours of monotone video. The challenges are a bit stolen from Cybernetics. Additionally, instead of teaching concepts, the challenges at times have CTF level jumps through obfuscation. A large amount of time was wasted trying to understand how the bots work. This is an unnecessary restriction that inhibits learning and gives a trial by fire approach to security. I'm for "trying harder", but I'm very much against this CTF approach to learning and encourge OffSec and HTB to explain how any simulated phishing exercises work instead of hiding behind mystery.
I'll update this when I hear back from OffSec in 10 days.
## Update (February 22nd)
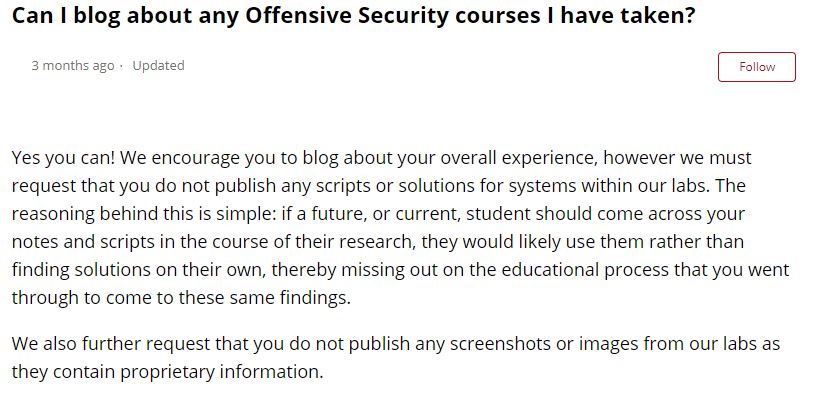
So I didn't pass. They are very upfront that they don't provide feedback or grading.
Regardless, I asked why. This doesn't make sense, I should have passed.
They re-reviewed my exam (another up to 10 days) and have denied me again with a generic response encouraging me to read the FAQ. https://help.offensive-security.com/hc/en-us/articles/360050293792-OSEP-Exam-Guide

The exam control panel states:

I compromised the segemented file server and provided the requested proof.
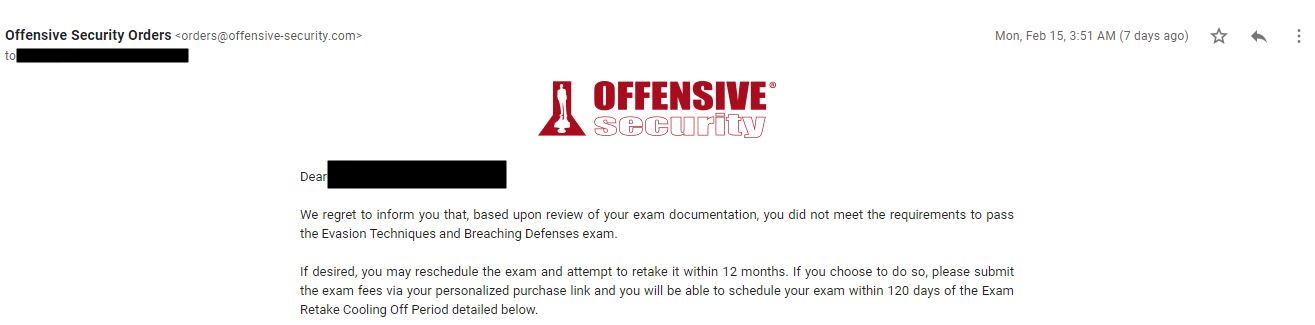
Now I am being forced to wait 30 days and to pay $200 to retake the exam.
I'm only getting generic responses from Offsec. I reluctantly signed up for the re-exam, but I honestly don't know what's expected.
If you have signed up for OSEP. I'm sorry, hopefully your experience goes better than mine.
Offsec, Try harder.
## Update Part 2 (March 1st)
It has taken weeks to finally got a response.
```
It is not sufficient to provide proof files from a command prompt of the exploited machine through RDP session.
```

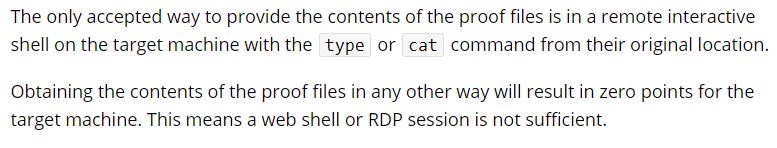
I think they are talking about this portion of the FAQ.
This is such a nit-picky and petty thing to care about. This is very poorly written and should be reworded.
To me using a cmd prompt on rdp session where I can remotely execute commands and get back a response qualifies as an interactive shell.
This wording only implies rdp+notepad as not being allowed. I used the `type` command to show the file.
My exam is tomorrow and I would have easily done this again.
I feel cheated and want a refund for my re-exam fee.
I'll take a new screenshot of a beacon this time, but this is largely a waste of my time.
I'm still worried I'm going to unjustly fail. I have asked mutliple times for them to update their wording for what they are looking for and have gotten no response.
I made this blog post because I felt I needed to warn people how shitty of an experience this has been. Don't take OSEP.
# Update Part 3 (March 3)
Exam day is here. I had to wake up at 3am because offsec has terrible time availabilites to start my exam and to verify who I am.
I got my new screenshot and added a stupid amount of detail to my report.
I really don't want to try and solve the second path just so I can acquire more points to help ensure I pass.
# Update Part 4 (March 4)
I solved the other path, took an abundance of screenshots, and submitted my final report. I'm really unhappy with Offsec.
# Update Part 5 (March 7)
Got an email saying I passed.